
How Your Red Team “HID” in Your Readers – ESPKey Attacks
DirectDefense performs Red Team engagements for its clients as a standard service. During many physical Red Team engagements, we are met with physical access control systems that use RFID or NFC to provide authorized users access to certain areas of buildings. These systems are often used to control entry into a building, or control access to sensitive areas such as data centers or wiring closets. Now, one could grab a card credential cloner like a Proxmark3 RDV4 and bump into a target to clone their badge. One issue is that this is not terribly stealthy and prone to issues such as failing to clone the entire card, or just using the incorrect cloning technique depending on the badge technology itself. Additionally, you may bump into someone who does not have the proper access.
A more covert and effective method would be to take control of an existing reader, a process that is very similar to skimming. This method uses an existing facility reader to read and clone all badges as it reads them. This ensures the acquired credentials work for opening the door. But how does a Red Team leverage an existing reader, that is installed in that access management solution, against itself?
Red Teams can perform attacks against the communication between the reader and controller with the controller being the device that validates the credentials on the backend. If the communication between the reader and the controller is not encrypted (most aren’t) then the Red Team could leverage a device called an ESPKey.
Here is what an ESPKey can look like (letter postage stamp for scale):
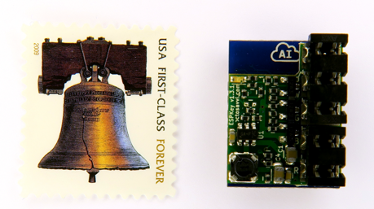
An ESPKey can be installed very quickly on the wires coming off the back of the reader. How does one get access to the reader while it is mounted on the wall? Well, if it can be mounted then it can surely be unmounted the same way. There is usually only one screw on the bottom of the reader. Whether it is a security screw or not doesn’t really matter as the screwdriver head that matches the security screw can be found online. Hopefully the Red Team does their homework and recon before this point.

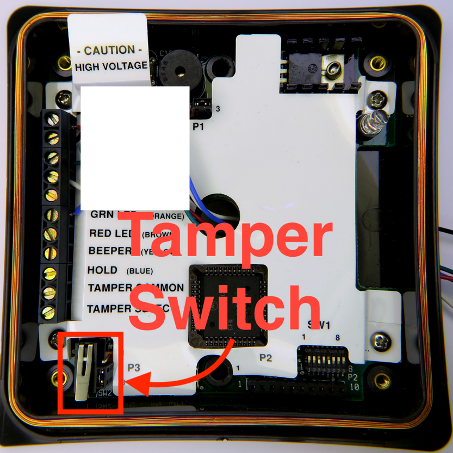
Some of you may ask, “But what about the tamper sensor on the reader itself? Surely that would detect the reader coming off of the wall, right?” In most installations that we have seen in the field, the sensor is never even wired up by the contractors that installed the system. The security team would never know that their readers are not actually installed properly unless the system went under a physical security review or a Red Team engagement. DirectDefense can audit these sensors with your security teams to ensure they are being monitored properly and review the response procedures to ensure that the readers are properly inspected before returning the reader back into operation.
Here is an image of what a tamper sensor may look like. This one is not wired up correctly:
So now that the Red Team has gained access to the communication wires going into the wall it’s time to install the reader. This just takes a “punch down” tool to the wires to install them into the ESPKey. Here are some images of the punch tool and what the ESPKey looks like while monitoring the communication wires:
Here is a covert pocket-sized punch tool:

Here is what it could look like once the ESPKey is installed on the communication wires:
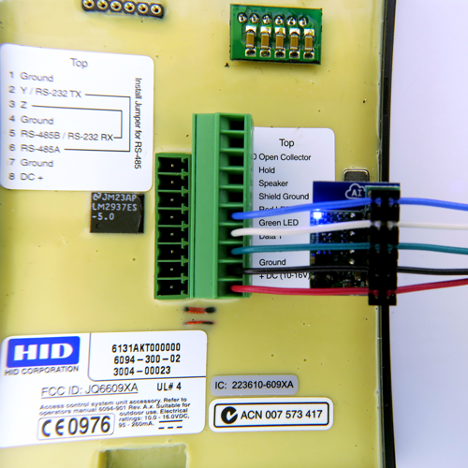
Now that the ESPKey is properly installed, the Red Team mounts the reader back on to the wall with the ESPKey concealed behind the reader within the wall itself. At this point the reader’s communication is now under the control of the Red Team without being detected. So how does the Red Team interact with the ESPKey now that it is behind the wall? The ESPKey has internal storage for recording so the Red Team can come back later and inspect the logs. It can also become a wireless router or connect to a wireless network to be controlled by a phone or portable device. Here is a screenshot of recording a badge that an employee just swiped:
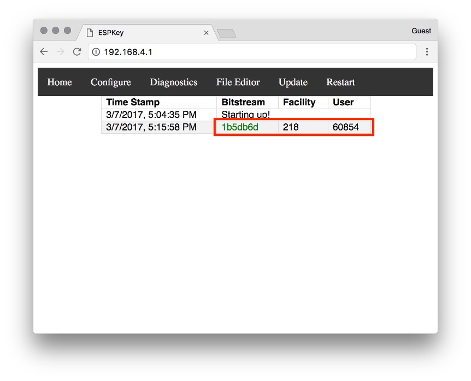
The employee badge is set to facility ID “218” and the unique ID is set to “60854.”
Some access control systems use the badge and a PIN to authenticate the user. For multi factor physical authentication mechanisms, the ESPKey can also read the PIN code from the communication wires as well. In this below instance, the employee swiped their badge and then entered the PIN code of “8247#.” The pound sign is represented by the letter “b” but could be different depending on the reader. You can determine what each button represents by hitting all the buttons on the reader after installing the ESPKey.
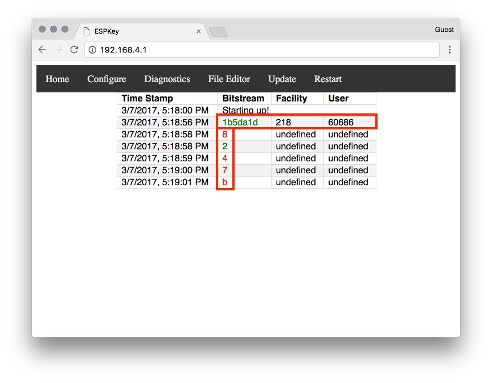
Now that the badges have been recorded, you don’t need another badge to clone to unless you want to use those credentials on a different door not currently connected to the ESPKey. Just ask the ESPKey to replay the badge data again down the line with the push of a button. This saves the Red Team from having to carry around additional hardware while in the field for more covert operations.
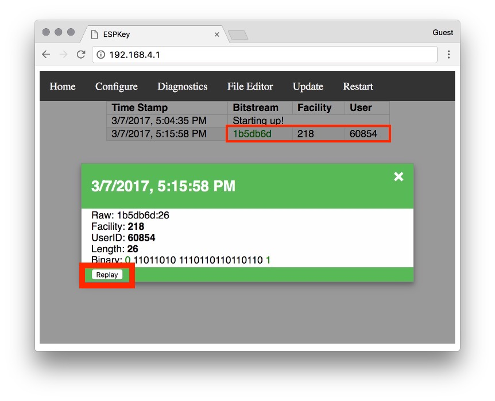
This is how a Red Team can gather multiple badges and PINs from each reader and use the readers to ensure you can trust your credentials and your buildings’ safety against themselves. Have you audited your physical security controls lately? The results could surprise you…
 Back
Back
